Update: 2022:
GPG is now integrated into Thunderbird 🙂
And it works pretty okay, thanks all involved 🙂
- https://www.linuxbabe.com/security/encrypt-emails-gpg-thunderbird
- https://support.mozilla.org/en-US/kb/openpgp-thunderbird-howto-and-faq
Update: 2021-01
Mozilla changed a lot in Thunderbird, Enigmail and other addons are not working anymore.
Update: 2020-10
apt-listchanges: News
———————
thunderbird (1:78.3.1-1) unstable; urgency=medium
The Thunderbird ESR series starting with version 78.x has finally dropped the
support for legacy Add-ons and also for legacy WebExtension Add-ons.
By this some packaged Add-ons within Debian, but also some external installed
Add-ons might not working any more!
The very popular Add-on Enigmail, which was providing OpenPGP support within
the Thunderbird application, isn’t getting further development as an external
Add-on due a consequence of the changed Add-on API.
Instead Thunderbird now has Built-In OpenPGP support since version 78.0.
The latest version of the Enigmail Add-on (>= 2.2) will provide an migration
wizard which helps to migrate the existing OpenPGP keys into Thunderbird.
Please have a look for further information about Enigmail on the project
homepage and the Add-on website.
https://www.enigmail.net/index.php/en/home/news
https://addons.thunderbird.net/en/thunderbird/addon/enigmail/
https://wiki.mozilla.org/Thunderbird:OpenPGP:Smartcards
You might also want to have a look at README.Debian for more information.
— Carsten Schoenert Sun, 20 Sep 2020 8:40:00 +0200
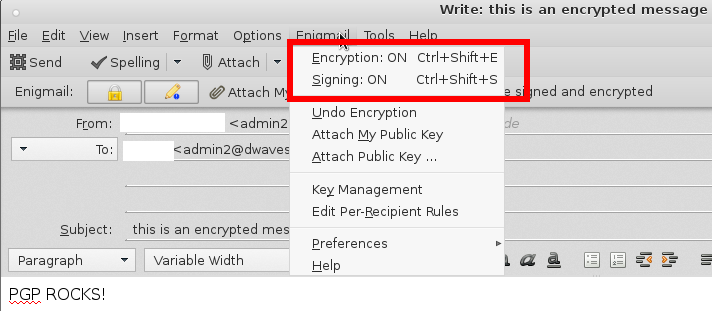
Update: It will now also encrypt the “subject” parts of mail.
But not the “From:” and “To:” Meta-Data.
Problem: DO NOT TRUST THE OFFICIAL PGP KEY SERVERS! (like Thunderbird’s default: hkps://pgp.mit.edu)
They are slow and can be compromised!
Just simply attach your PGP Key to your PGP encrypted and signed message.
more meta data that will be send in clear text: what OS and mail client you are using: (often wonder why this is send… it’s fun for me to find out what OS/Mail-Client people are using… but who needs this info? i mean an attacker or AI could try to find exploits for exactly this software and try to send you attachments like: evil.pdf that is tailored to the mail client you use)
Exact Date: Thu, 25 Jul 2019 13:23:52 +0200
OS-Used: User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101
Mail-Client used: Thunderbird/60.8.0
Update: 2018.02: This combination works very very well:
gpg --version -> gpg (GnuPG) 2.0.22
mirror backup download link: https://dwaves.de/software/enigmail-1.9.9-sm+tb.xpi
sha512sum: https://dwaves.de/software/enigmail-1.9.9-sm+tb.xpi.sha512sum.txt
well yes ok take 15min… or 30min…
also tested with Debian 10 under version:
Snowden has used it: Why this is important
Recent government spying revelations have shown us how hard real privacy is to achieve, and how little of our information is really safe.
GnuPG is one of the few tools that can offer real protection.
Yet it remains popular primarily in only hi-tech circles, despite it’s availability on Windows, Mac, and Gnu Linux, its ease of use, and the fact it’s free of charge.
We need to introduce new people to GnuPG and help them to start emailing safely and privately – the new GnuPG website will play an key role in making strong crypto desirable and accessible.
Why is strong privacy so important?
Faith in the privacy of our communications is necessary for:
– Guarding trade secrets
– Meaningful and fair negotiations
– Protection and advancement of human rights
– Academic exploration and development
– Political freedom and democracy
– Proper development from to adulthood – childish mistakes belong in the past
What makes GnuPG so secure?
It’s Free Software – anyone can inspect its source code and check for back doors, and security experts frequently do. It’s made by leading experts who were originally chosen by the German Government for their aptitude. It’s build on rock solid cryptography principles that have been adopted industry-wide, and uses the OpenPGP Open Standard for compatiblity with other applications. It’s so widely used that hundreds of companies have a vested interest in checking that it works the way it should. Unfortunately that doesn’t mean they choose to donate to the project or support it in other ways. And it’s even used by Phil Zimmerman, father of strong email and voice over IP encryption.
https://en.goteo.org/project/gnupg-new-website-and-infrastructure
If you are using GnuPG to secure your data – either on server based systems or for example by email applications on the desktop – it is in your own interest to keep this software alive and well maintained. You can help GnuPG and thus yourself by:
- Donate to the development
- Purchasing a support contract
- Engaging us for custom enhancements
src: https://g10code.com/
if you wanna send them an encrypted mail look here: http://werner.eifelkommune.de/mykey.asc
In short: PGP works with 3 files
pair of keys:
1. public (pub.asc) (distribute that on the net)
2. private (pub-sec.asc) (keep that file private e.g. on a truecrypt encrypted container on a usb stick that you wear with you or store away savely)
3. revocation certificate (rev.asc)
you will generate all three in the following process.
PGP Concept:
if you encrypt something (mail, file) with your public key – it can ONLY be decrypted with your private key.
This is why NSA wants to get quantum computers so they can crack that too.
The public key goes public – on your website – attached to your mails or you can upload it to a keyserver, where people can download it again and encrypt mails that they want to send to you.
mine looks like that:
-----BEGIN PGP PUBLIC KEY BLOCK----- Version: GnuPG v2 mQINBFflhfUBEAClOYclsa3Fij6QWXl9ASbSx9L2f5Rm1MDN7ZyAK9tqp3+YDc7L elIBVN2uyz8C3uzrCHDUNw2FOEMDdOrVpNUUz25DVGTH8XzlGpLhqhRG8tCzGt5C Ay3r8vQN5IgjMD71rhs9YCHBRYC1a/syINKn7Nge+ITTvVyK3ITVzgDC/OvoSNE/ xpZVzq+M9MxOC70Sfe9JrlsUN3Wo+fYdze7dVvs3LahJeCE8vWcvPKlrYF3ADlBb PvgmvoUZBg09HbsMmG+fntc0H9t06yPaPeMeNRcZiJP1AR2fYCafodadVTpKoxPE q6z+yA7VvIc2sl64rAzoULbemG1A4JL6fl5KBG3y/S3t02sT5sADJPUoqXdmDriU NBtqd2vcvtiCPgXTG8P0YjqSbvhODmm30bx2oVg6KjREW7A33oehdpTleeL6jhdx sq+G28CsFwN/erQG/uOBo8BvFXkcc6NJOtStbhwPbXY7Q1mBXZoxGz3MhnE9eEM6 hG1/ZRVMnVj5kbpH1l0fjRWnNSW2YLHSPYqTA3FFf8m7LAku/gWnD3g81C85XRuA uFkSQvM2DlT/pg1Q+vZf8c+PPchDlGKvFTgYrDEGSFTUvWAmjsr1dsD0z1G4Phdh /Pk747H07nNSETx+ttp8UvCtMRYZAtAJuU1olydgW/bt/RNKJuL0wXfm0QARAQAB tCFEYXZpZCBGb3JzdG5lciA8YWRtaW4yQGR3YXZlcy5kZT6JAj8EEwEIACkFAlfl hfUCGyMFCQlmAYAHCwkIBwMCAQYVCAIJCgsEFgIDAQIeAQIXgAAKCRDm/85cYxpM X30dD/9yntVQC1g4fQyci9btICcIDsrXEQ0IUEcoOnT8IfoNJJjl1mtQ2a1DKTOI Q4xaBGBp+JpCguUl06NotxBLFBmbqL5mQ5Xee2x8zlFpO74MKSKUAX8k6M77C2R+ 1t6vPEGJYUHpz67KX8csGRJ8+qWS4vpUnCgFluzFvKGMzJCMrrO+P2lXKYyrr6yD iFog9qOsNB9uaIWrEQYHf0imbHcSNpFtS3chMNVhpDF1JXEmRsa5C8UwAzXK6k0a ADDwSVEfiQ8Zb8krKeD83eGyFFKXL79bWInLqwr1BwrsSZ1jSyIUGgFldDNJS4KU AZFxtdfMNh7V7MdllEX+MsqXIvKa+KsvdESaHKH9OcLMbKHTI56wDON5bj5nGY0x 95WhEw2b04d8FT6sH3/6gBV7BRYCT8sdb3UaGXLCrbqb5hT/T8OtM60Nf1/ySyy2 U+P/LLcphZei9o5j0BmDDrmlRTilvhzx/+dmTe0wANZVb8ry9UA/WnhI6ZyeNtsV AfwY9+j18rA+ReH97UTX994hwHSn7k4T5huVxbpT4sOzSxQGEIHeQV0jlQlhwj/+ 9W7ygpwo98GDMW67ztoNaFGd0CK+Vgpnisc1uxhSTbcwYO6zaRYT1dxclHGMvW6t zjLG15kukuEkT0ojKrKRz2jYsAZ0BQMxJlvxDCnlagaDKgGalLkCDQRX5YX1ARAA qHnqDNeYz6wNkWmhqf++FennfcNAYqW9O4XgT6io/7YRyXGAG84bfTsCU71INkKg N7bQ/tDyZBeMIxOaS+EXGexJLhclJeac2LSyPYWRaK9bcoWwUBdT/GYOqnS1he4M +GPzgB6XHLToG3iyrpF3wis5NaEKA3pyx6rus4O+H32+lCTtEbeWV5vYyorql6I8 TzIuUsXt2UUeU/6ibW3mN4st4fr7UjgwY4B+DJ0O3HAFAFne4godcUsLfGkKm6pA lpyVV15OCPZ2XOpFBvqu8mLEKSjilVdPGaSi0l8rfTmFj+0k9uOvOr7tQnpk70KG 8l4ehK6gs1+ysVZPc7QwsPZstmYiXAwRL0hvLMTdaiZPpmfIZ3HdyhrieHG0pvnm UwHR7IkuLwSBQdv3CmF5AY7fNw77Q8LC9u1TriE7e1zpevZe2BJJaphRjiwrT+cT flPlnd5CmleWl0sh5RFIMfdqfuUyyuM4bTY0ORueC7QmzrkYcDWly/Uc/T/FkM89 kf8rQI9HQCnKx7yqGSNi+9H2Ayol5c1ekU0gyAfvgfUWATPm1gfpxZbG0S+OY/DC JsJCcYzUcm+CFaf1wBxKzImKLZ6aExVevHUzeZlbY4NliXul6uKA1K0qoP3hxvs0 cNtUTIRMd3SeqjLBN4HMy8UXQL4GbIuORfKwbckw4j8AEQEAAYkCJQQYAQgADwUC V+WF9QIbDAUJCWYBgAAKCRDm/85cYxpMX2mTD/9SeQ3pkecYQXDgCYhCffgHykpw d61nukAKx/ORHyoxKyQKu1yIN4Vdvpby5owyl5KXSYJA2Rz5OnmmKI7z8mYb8MlE 8vgQK3022628zUJX2Ykw94GuHvXYyHejdpiG077u+3RyZXbZv8rDkF+eMvgxoz0T SPzHqAHOn78gi2KJAEScB4QSzwuWSS2F/+DkP9omrYLWqmOHhsEWS/+8QKYcRdUi kWC9hSgZeLbxsbn5YKsUS8zfkIAqbBfZ4jibUZlDFpj4Lq9iYeMqbIVPS0sQSTQR SoEcA4DbhDzfUGsI59CZaJxN5KhQg2+Xx7hu46fc92lEayaBpsCZrmDgcc3d3VfY fXmmCkMWJBg7qcVeGmvCGMSiqO/4jtus69WP1f++rbHpe8FZvZwuiqivI0A28WW3 /+Ndrq6VPgZQwkdsdpohI70wMJ9EMqtxGDLEVWUsME4o7lSU3rqZyLjtqe4rt5Hj sN1goolTJ/5BYDPxZEHk0yYoWWeC92NsBbHOLTrLwAmwq2SrfIrAnrtL5c7yJ4rA ErPOb2bdCCVDWzTDPpN/9YNs5Ki4gstQy1ooBDbqiDUaUEHg2jSfK7APQdCVd5Kz nsj+Cr+5ej+n/WxgK/Pl7Oq2ZlS/OV7Ae+XusC7pl/CPtH+irV0upqP1HbbaJXKP lTU0V05xGcIAuPZ1JA== =Z+RW -----END PGP PUBLIC KEY BLOCK-----
There will be a third file called “revocation certificate” that you can use to disable your public key – in case someone stole your private key and it’s not safe anymore to send you encrypted mails with that key.
We will go through that later.
With PGP the NSA can still see who communicates with who (meta-data) but can not mass-analyse content.
You can set this up pretty fast.
1. get and install PGP Plugin
uname -a; # tested with Linux debian 3.16.0-4-686-pae #1 SMP Debian 3.16.36-1+deb8u1 (2016-09-03) i686 GNU/Linux # under debian linux this works as easy as apt-get update; apt-get install pgp; # should install gnupg yum install pgp; # should install gnupg in CentOS7 gpg --version; # check version gpg (GnuPG) 1.4.18 Copyright (C) 2014 Free Software Foundation, Inc. ...
2. get and install icedove/thunderbird
# under debian linux this works as easy as apt-get update; apt-get install icedove; # rebranded version of thunderbird
or manual download thunderbird https://www.thunderbird.net/
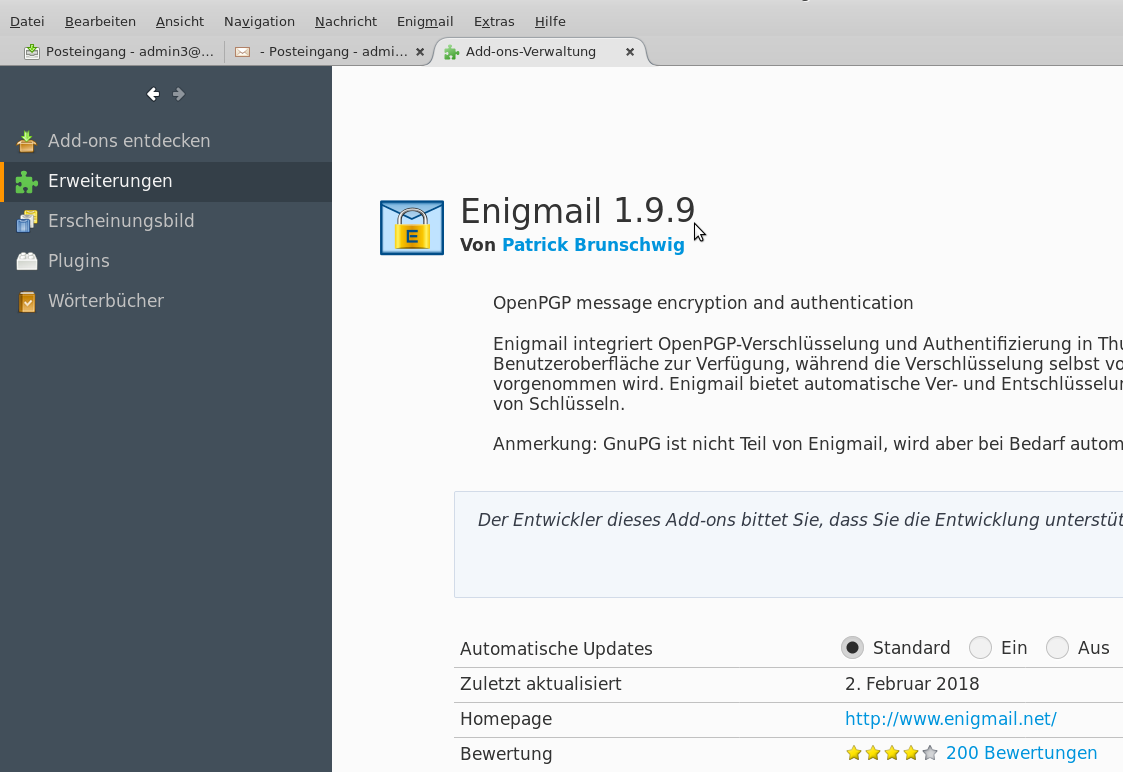
3. install a little older version of the Enigmail Addon, because the newer one gives ugly errors (under Debian8 jessie 3.16 kernel and icedove 45.2) like this:
the older version of Enigmail 1.8.2 works like a charm with this setup.
Download it from here: https://addons.mozilla.org/thunderbird/downloads/file/310358/enigmail-1.8.2-sm+tb.xpi?src=version-history
or download mirror: https://dwaves.de/software/enigmail-1.8.2-sm+tb.xpi
download & verify:
hostnamectl; # tested with OS Icon name: computer-desktop Chassis: desktop Operating System: Debian GNU/Linux 10 (buster) Kernel: Linux 4.19.0-6-amd64 Architecture: x86-64 # become root su - root # install pgp apt update; apt install pgp; # become non-root (proceed as non-root user "username") Ctrl+D; # root logoff # go to one's software repository cd /media/username/external_harddisk/software # download addon straight from the source wget https://www.enigmail.net/download/release/2.1/enigmail-2.1.5-tb.xpi # download gpg signature wget https://www.enigmail.net/download/release/2.1/enigmail-2.1.5-tb.xpi.asc # download public key of author wget https://www.enigmail.net/download/other/Enigmail_public_key.asc # import the public key of author gpg --import Enigmail_public_key.asc # start verification process gpg --verify enigmail-2.1.5-tb.xpi.asc # user should see the important part gpg: assuming signed data in 'enigmail-2.1.5-tb.xpi' gpg: Signature made Tue 31 Dec 2019 04:29:51 PM CET gpg: using RSA key 4F9F89F5505AC1D1A260631CDB1187B9DD5F693B gpg: Good signature from "Patrick Brunschwig <author's mail (that spam bots will collect from websites)>" [unknown] gpg: aka "Patrick Brunschwig <author's mail (that spam bots will collect from websites)>" [unknown] gpg: aka "[jpeg image of size 13251]" [unknown] gpg: WARNING: This key is not certified with a trusted signature! gpg: There is no indication that the signature belongs to the owner. Primary key fingerprint: 4F9F 89F5 505A C1D1 A260 631C DB11 87B9 DD5F 693B
manual install addon in Thunderbird:
this file: enigmail-2.1.5-tb.xpi
sha256sum enigmail-1.8.2-sm+tb.xpi # should be in any case like this, no matter from where you downloaded 3dfd29a12fc36c5780574bdab67fb61d63e65e67671d14921749187f7af1639f enigmail-1.8.2-sm+tb.xpi; # newer version recent in 2020-02 sha512sum enigmail-2.1.5-tb.xpi 832eb3d8d081fefc02709fd53f107b135c9d73c84fb2425874d69095b5a0b391ffe68bbc30f1a56912c24714ffc85434e864c2cc13be8f05a44c10ae16579a50 enigmail-2.1.5-tb.xpi
4. Start icedove/thunderbird:
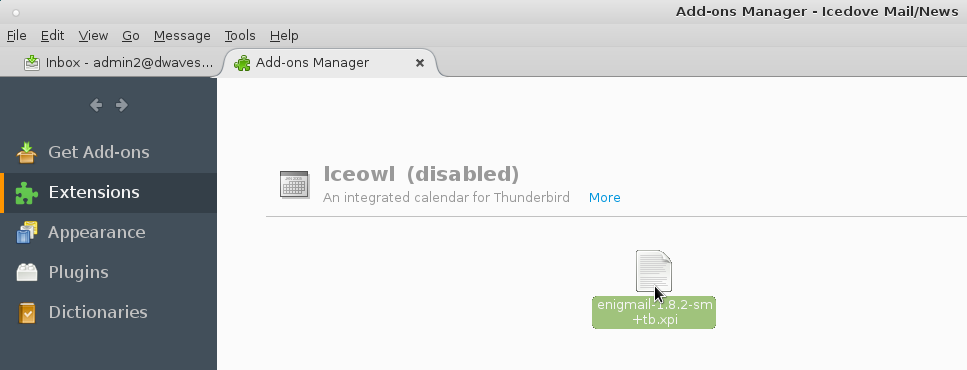
5. drag and drop the enigmail .xpi into the whitespace of your addon window of thunderbird/icedove.
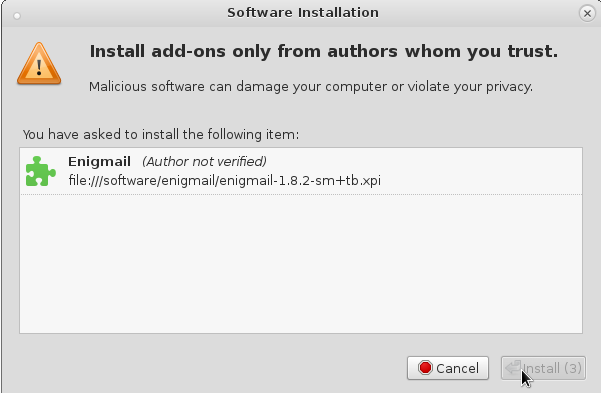
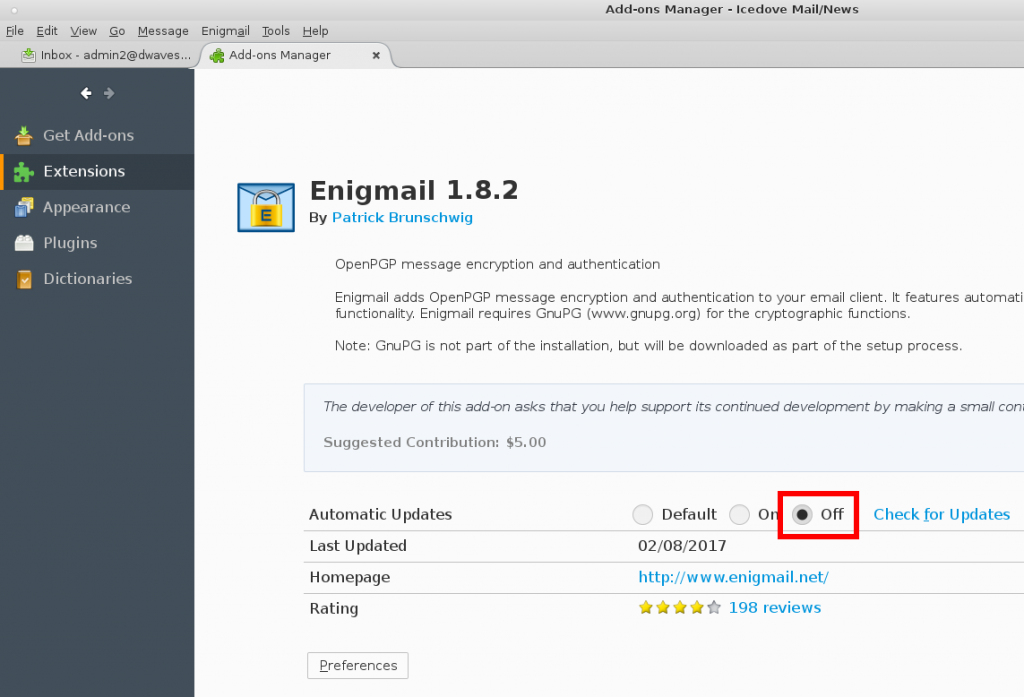
MAKE SHURE TO DISABLE AUTO UPDATES! OR YOU WILL END UP WITH A BROKEN VERSION 1.9.XX IN A MATTER OF SECONDS 😀 (should be fixed by now)
one can safely click on “Install” after 3 seconds…
one will have to hit “restart now” button to restart icedove to activate the plugin.
generate new keypair or restore from backup:
restore from backup: “your secret key has missing trust”
one surely has backed up one’s home directory (/home/username) before reinstalling a system.
in this one will find a directory .gnupg
that can be backed up like this:
cd /path/of/home/folder/backup/username # backup the folder tar fcvz .gnupg.tar.gz .gnupg # move folder into place for restore mv -v .gnupg.tar.gz /home/username cd /home/username # unpack/restore overwriting the existing .gnupg folder # restoring one's keypair tar fxvz .gnupg.tar.gz
generate new keypair:
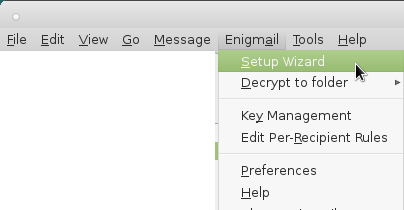
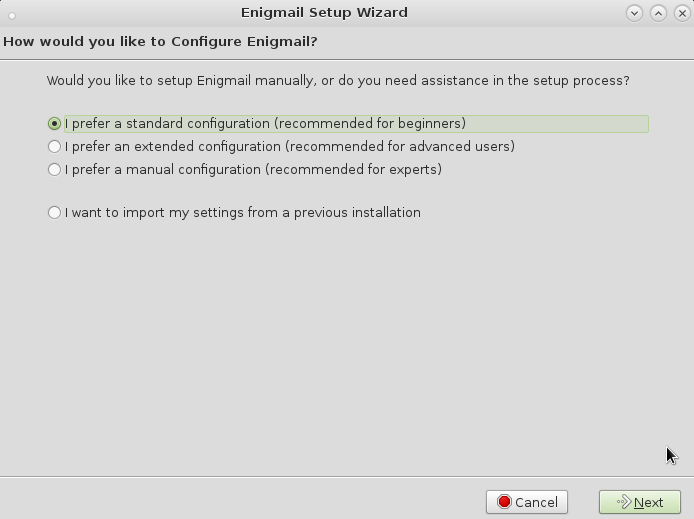
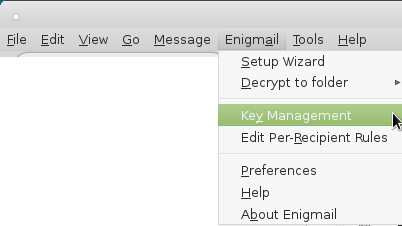
6. one will have new menu options “Enigmail” -> if you do not have yet any PGP keys click on “Setup Wizard” will guide you through the process…
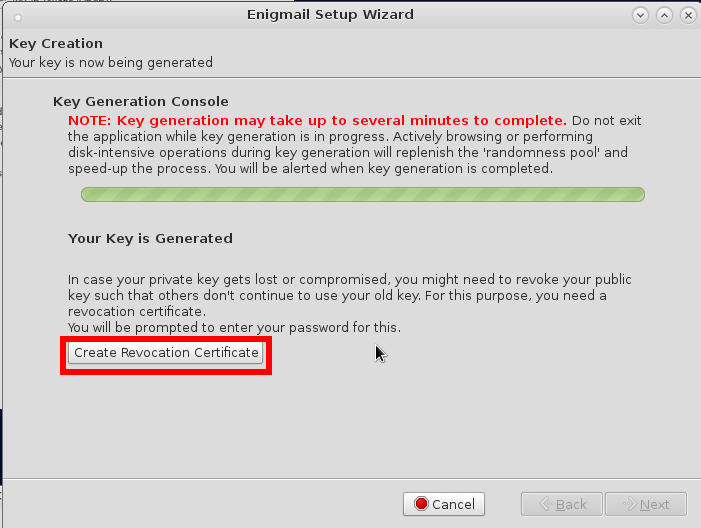
save the revocation certificate on the truecrypt container on your usb stick that you later put into your save…
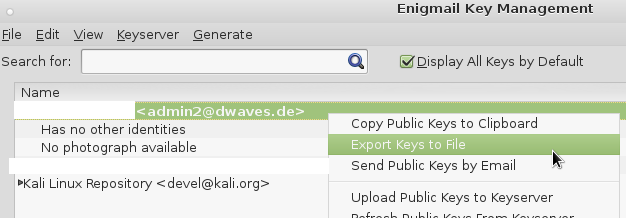
backup / export your keys to the truecrypt container on your usb stick that you later put into your save…
you will have to click “Export Keys to File” twice, once for your private key, second for your public key…
you will have to give a passphrase that unlocks your private key whenever you have to decrypt messages that were encrypted with the public key of your key-pair.
7. if you already have some PGP keys that you would like to use: (and savely stored away on some truecrypt encrypted usb stick)
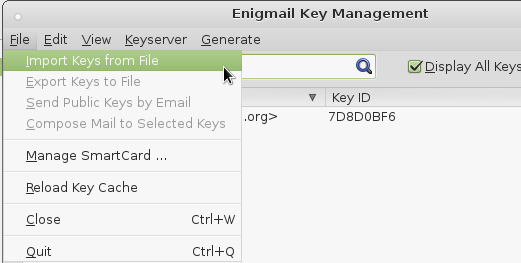
you might want to import them this way:
you do this twice:
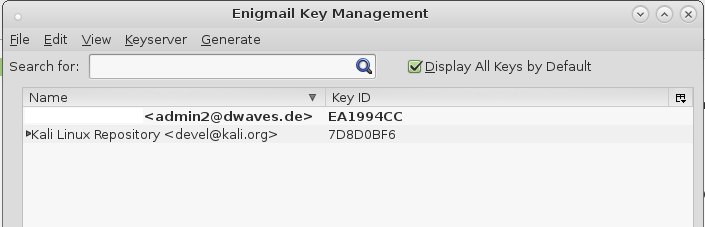
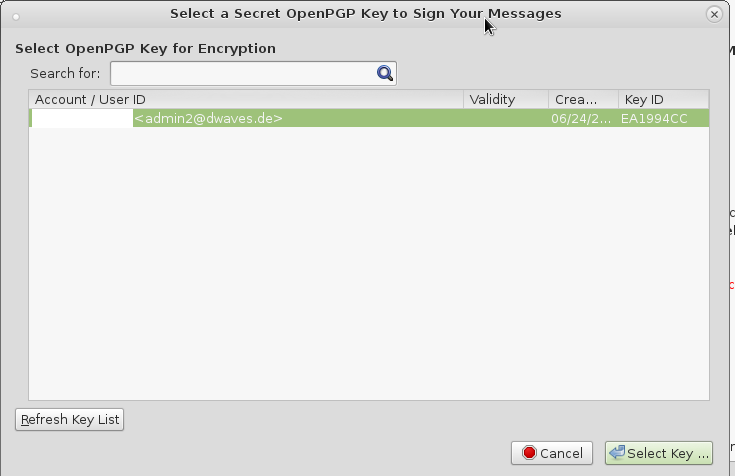
- first select your public key: “Your Name user@domain.com (0xEA1994CC) pub.asc” file and hit import. You should have a new entry in your list of available public keys.
- you again go import keys from file and import your private key “Your Name user@domain.com (0xEA1994CC) pub-sec.asc” and now the entry in the list turns bold-black.
DO NOT SELECT YOUR REVOCATION CERTIFICATE! OR YOU WILL REVOKE YOUR KEYPAIR IMMEDATELY (WITHOUT BEEING ASKED).
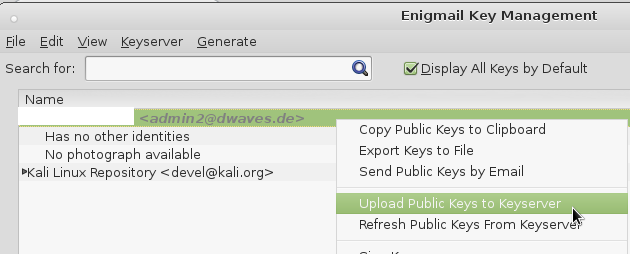
you now have successfully imported all your files and you could publish your public key to a keyserver like pool.sks-keyservers.net:
so people can conveniently download it again and have not to search all over the internet.
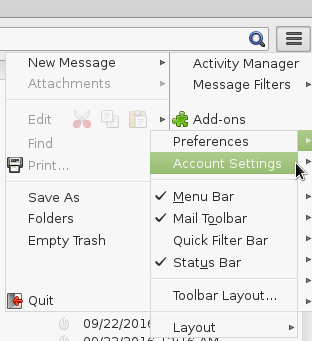
8. click on the “three stripes” on the very top right -> Preferences -> Account Settings
click on “Select Key”
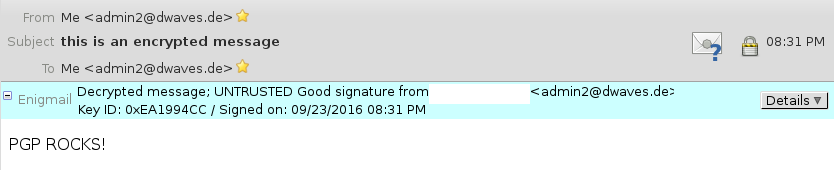
9. test if you can send yourself an encrypted message and decrypt it again.
and hit on send, you will be asked for your passphrase which is used to unlock your private key to encrypt the message. (same on decryption)
TADA!
If you hit Ctrl/Strg+U (Source View)
you can see how the NSA Agent from the Matrix would see your message:
Return-path: <user@domain.com> Envelope-to: user@domain.com Delivery-date: Fri, 23 Sep 2016 20:31:06 +0200 Received: from [46.182.143.123] (helo=[192.168.178.123]) by dwaves.de with esmtpsa (TLS1.2:ECDHE_RSA_AES_128_GCM_SHA256:128) (Exim 10.5.12) (envelope-from <user@domain.com>) id 1bnVFa-0001hX-Kc for user@domain.com; Fri, 23 Sep 2016 20:31:06 +0200 To: <user@domain.com> From: <user@domain.com> Subject: this is an encrypted message Date: Fri, 23 Sep 2016 20:31:05 +0200 User-Agent: Mozilla/5.0 (X11; Linux i686; rv:45.0) Gecko/20100101 Icedove/45.2.0 MIME-Version: 1.0 Content-Type: multipart/encrypted; protocol="application/pgp-encrypted"; boundary="oxxvFWgDDrn5xwiSmRHIvAjA3W5NX3ird" This is an OpenPGP/MIME encrypted message (RFC 4880 and 3156) --oxxvFWgDDrn5xwiSmRHIvAjA3W5NX3ird Content-Type: application/pgp-encrypted Content-Description: PGP/MIME version identification Version: 1 --oxxvFWgDDrn5xwiSmRHIvAjA3W5NX3ird Content-Type: application/octet-stream; name="encrypted.asc" Content-Description: OpenPGP encrypted message Content-Disposition: inline; filename="encrypted.asc" -----BEGIN PGP MESSAGE----- Version: GnuPG v2 hQIMAydU4bQrUY9wAQ//QhXd4Zl3j3+N2sySXORaepSY2sQ+q1pHJ3l9nZtvB68s eoU3HeFj7O2AnjzXmH3KSM0rL3xPgKr2HVX1z3KDtfaOktzc4WBLcAXccDEAlhTk LksdPDnNZcifatO29bdITaNgiMpl7Q/8ShvzY91upfTlaqLcrAvk7KtAIV8D9hjH eSy3Nfh5b1K+1Lm9VTS2yd2MgO5+JTHovqPZueUvQL2lwi7jWTeu7TtSfMYjaBOU c2zX4IIJmA52GyzkiEA5DMHsmPgZzzKxKmJur0gQQhIMuz4x/3PllnKVFppE4E6x iJYylK1GbCEhzdG/xY4KW+/jSNVl/nEilxwoQH3qBIaJS/JoY6MTffkMiACgNdsx WU+vw/AOXzJUelJq9qEJvFqWa8iJshUmmoKg8A0gelDfM3O9GnJo0lXcQCpq7pVY gec5b7rG1PTpFWry5z86wAoaS8M0cj7jNJmq8stIJra7H0iuo0zFAqgHmMliD5yJ QbW00dSS07B+Pk/MjlbbLlpqTvqRUFJv7QMVM2foyBWsEri3kRKm1NfQrpHHojXt jSVaa+RA3B9V/iFO0hUjEOMNu9RB8RQrtlcxjHeaCQ0/waxgNrin8ccHPehOgz1T B3A8PikPZdu8WYZaQAVQJwQjOVnP5VRAw4Zyc3GOn4NnIfpHRS2H7DoU3t7Y1sHS 6gF0uQ1YUGoCmMiLx1zUSASqsHesYCPcECJL/vNh/rvUezAiUK9CevWssF+/9w9W OEOtC6QRyHlJswMwMHXlVXYRhaT+5q/KxHngSfzTUeQUTMCaq2PcRLr7I085G1xB 6VoVW8N0AYYP46n1X1aE91/wE+W/PKaKnGV+HV8CJFFUNyRokfQJrjKpN+m737r5 N6bUsU2iq4/chW+Bud8/oNnMfxmsFRcWZSjase4edi1dAAZ+CT/4Sfow+CHj9L1y xAWNF1ynkPJ6HkS2IH56b1ylYxuGjSgv2f4/c45TIuyJ8ymlPhfS5Ed9f38YCiqW FehrRzuGCshZlYOoodUW6kw4DsVtV4d81UBt39V5OqCf17wQo+xL492zzH5MARsf k5POjvuTy4Nn7X95zYWdgPRbhu5LIhflqLreGMxNbPoqTVDPQn1dQPgax0Q3hFhH VdGOQFQXtf6LTjGztPqDU6Q1jF5N2zNASCjMniZ8KUE5Bbk4ZQK3OpKbN8I4JmKF igXNkm3r7a/uGDT28BN+cFpRoPzq0YjBJuu8V/NQdutxRuowdsx/GEAR2IodE3EF PaeyOqCjwLzJsy01l+t4X7CTZ/X0HJFRj9Ksd3faHDXLcELg7BMZ7gHdpCWarBkA bijfMD8kA5nzbyCqhChuzgCgASmtZnetSU9aWGwHrtemtKrwZAq3CfeXekslcuEH Ys7q1ZnHfH88pjuChEc02AUxWWVRybc4sj58JzwYSgPDVf3lzcXh5B4qRm58vVFU QzsOiG8QIqXk1OHb5DI3cdkXQC84Prf4ZODCVsV/4iCKMfSNl4J5H3RoBLbFHpRA GYLTcUY4J7WULebuhjaq0DLzl+bxZYd/4wAraFHyxcNZ5WSP9pXb1x44XJo0+46/ rwpOsjHKxDyf72iXi+KSYZ4PycbgcMI/8nONCP83rKdG82yjMC4qMKjh7l46uKZS VwiMz5Bed4XYb5VvatPxqciZ6Sl2NRQOVJH+P2RqwP/pLkBDynV1RU8Z7vw5MM/0 sGLDLgOfoWaSZousGrc4TbMqw9aV2XCqs0xE1pfqwSdhil7NKfNEmVY4aVnaMwwj dLgVJfdh/gnmYXyZ20nPvHcEV0Jj8WV5ZmCHTJDCkDECaMdO5EmsBYLAWuNzvAW+ 6trkJECBJAT6sRDENhFHHohZERpFl4l+pWhOMWrMOQz8AjCwQhfvCfTOW9NSTkui yL1vVaQbn4Q+hP7UKy4KbPFP81fMsBnp1Jzz76hYR2g5zFTSkCA/PH0YHMz/yMQd /VyEad3cfj770MgE9S4Zd33yYQY9+jkJTd0XjHjOvmJvWVajs0VF1e+9kHxFDiRH ryKroHCs2WC5XGomu3NOBlnA7TEuwA0w0qSt+MlkHqcgemXZUAXZX4AjDJJr8lQq 2Re+VVuTupLo4caIJlQRTJDhdGjLal2k8uf8iEcTCTcD0OGhONRpvVpcOf4/YOPh ciLGEP981fE+Cl+XOp9qF/4/BwRqShgCpMDAg7Yzv47TRbOHomgfM1vH4h74XtPb nMfoFv+M4jgHRKQWzU7shXNeb/l2Q1A1mL7iQmd24sqiSI36coDfozDrd3BVHdTB YBdvfMo4x1rH/cURAd4G7Xxw4wb2A8A97Ad9KUtNSTcnYKS87YgePEfQH8KQ0UHo zRt+pKGm9Ifu8FzcvVUF3xKGC73u/vL0kZR6ZEeVkdA7DVG/T5Kw2pFBwHdNumdz FjY5b58IbuHORxXOIkHbES7MJsu6DkagpR7Y9lGUDB8frU3ppEmVR1gzpWUdXji+ ZEFdM6M3FhWl8arFtMcNIuaAy+6uEvYFLImNtvz6mpfRqiFbaMX/+C7P0Acn+0pF 9iqgVjfgxxmalp86JUAOwI0sBpkLObtk7gA0NRj8YeJRWH4pT1slHF9aGKK8oYLJ KY6CsQW3c8sldBY7rn43Hg== =KsRr -----END PGP MESSAGE----- --oxxvFWgDDrn5xwiSmRHIvAjA3W5NX3ird--
as stated here: https://enigmail.wiki/Signature_and_Encryption
One important point concerns mail header security. Mail headers cannot be encrypted, nor included in the signature computation. This includes also the Subject mail header. Therefore, do not write any sensitive information in the Subject when sending an encrypted message.
Signature and encryption applies to the mail body only –- and also to attachments, if you chose so. That is, when you sign a message, no mail header (such as the Subject, Date, all Received headers, etc.) can be included in the signature. Also, when you encrypt a message, mail headers are not encrypted.
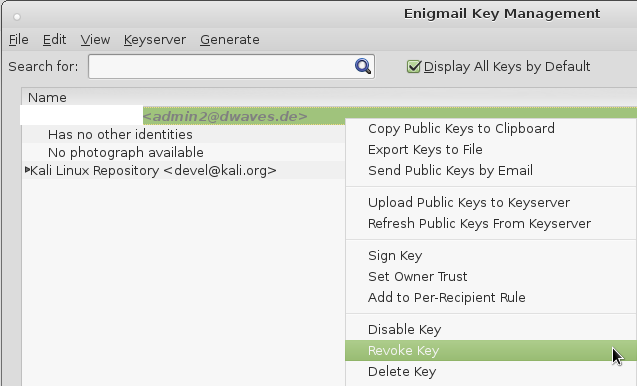
Revoke your certificate
If you have the feeling someone compromised your system and stole your private key.
You can revoke your public key.
this time select your revocation certificate file ending with: rev.asc
it get’s imported and you can r-click on your key and click -> revoke key.
Now it reminds you to also upload your local changes to the keyservers you previously uploaded your public key to make the revocation of your key public.
Thanks for taking the time.
this tutorial video was taken down… for whatever reason: https://www.youtube.com/embed/bakOKJFtB-k
Nice Video that explains: How PGP Works (german):
SCARY ERROR MESSAGE:
Enigmail Security Info
Decrypted message
Error – no matching private/secret key found to decrypt message
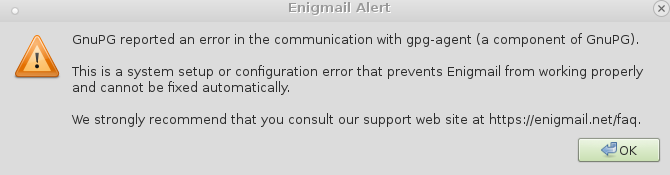
gpg: WARNING: The GNOME keyring manager hijacked the GnuPG agent.
gpg: WARNING: GnuPG will not work properly – please configure that tool to not interfere with the GnuPG system!
gpg: encrypted with 2048-bit RSA key, ID XXXXXXXX, created
“”
gpg: encrypted with 4096-bit RSA key, ID XXXXXXXX, created
“”
gpg: no valid OpenPGP data found.
gpg: block_filter 0xb78984d0: read error (size=5229,a->size=3181)
gpg: block_filter 0xb7897fe8: read error (size=10198,a->size=6102)
gpg: WARNING: encrypted message has been manipulated!
gpg: block_filter: pending bytes!
gpg: block_filter: pending bytes!
Note: The message is encrypted for the following User ID’s / Keys:
0xXXXXXXXXXXXXXXXX (Kali Linux Repository <devel@kali.org>),
0xXXXXXXXXXXXXXXXX (Kali Linux Repository <devel@kali.org>)
https://wiki.gnupg.org/GnomeKeyring
https://lists.gnupg.org/pipermail/gnupg-devel/2014-August/028689.html
Related links:
https://www.gnupg.org/howtos/de/index.html
Latest articles from Kristian’s personal blog (RSS)
- 2016-08-17: OpenPGP: Duplicate keyids – short vs long
- 2016-03-11: Norwegian government propose access to extended surveillance methods
- 2016-03-07: OpenPGP Certificates can not be deleted from keyservers
This website provides services for the SKS keyservers used by OpenPGP. A pool of keyservers is available at hkp://pool.sks-keyservers.net Information about the other variants of the pool is found in the overview.
If you wish to contact me feel free to send an email to the user id in the key 0x94CBAFDD30345109561835AA0B7F8B60E3EDFAE3
The HKP Pool
Read about the various pools
Keyserver statuses
Status information about the different keyservers can be found at the status pages
Interact with the keyservers
A simple way to interact with the keyservers is available at the interaction pages
The number of OpenPGP Keys
A chart showing the development in the number of OpenPGP keys by day. This is the maximum number of keys found on the keyserver at the start of any given day.
This site is developed and hosted by KF (Kristian Fiskerstrand) Webs
Amazing Stuff: Werner Koch
Werner started GnuPG in 1997 and still puts most of his working time into the development and maintenance of GnuPG. He has 29 years experience in commercial software development on systems ranging from CP/M systems to mainframes, languages from assembler to Smalltalk and applications from drivers to financial analysis systems. Werner is a long time free software supporter and co-founder of the FSFE. With the support of his brother he founded g10code GmbH in 2001 to make GnuPG development his profession. Werner is full time employed by g10code.
src: https://www.gnupg.org/people/
From Wikipedia, the free encyclopedia
| Werner Koch | |
|---|---|
|
Koch in 2015. |
|
| Born | July 11, 1961 |
| Residence | Erkrath, Germany |
| Nationality | German |
| Occupation | Software developer |
| Known for | GNU Privacy Guard |
| Website | werner |
Werner Koch (born July 11, 1961) is a German free software developer.[1] He is best known as the principal author of the GNU Privacy Guard (GnuPG or GPG).[2] He was also Head of Office and German Vice-Chancellor of the Free Software Foundation Europe. He is the winner of Award for the Advancement of Free Software in 2015 for founding GnuPG.[3]
Journalists and security professionals rely on GnuPG, and Edward Snowden used it to evade monitoring whilst he leaked classified information from the U.S. National Security Agency.[4]
Life and work
Koch lives in Erkrath, near Düsseldorf, Germany. He began writing GNU Privacy Guard in 1997, inspired by attending a talk by Richard Stallman who made a call for someone to write a replacement for Phil Zimmermann‘s Pretty Good Privacy (PGP) which was subject to U.S. export restrictions.[2] The first release of GNU Privacy Guard was in 1999 and it went on to become the basis for most of the popular email encryption programs: GPGTools, Enigmail, and Koch’s own Gpg4win, the primary free encryption program for Microsoft Windows.[2]
In 1999 Koch, via the German Unix User Group which he served on the board of,[2] received a grant of 318,000 marks (about $170,000 US) from the German Federal Ministry of Economics and Technology to make GPG compatible with Microsoft Windows.[1] In 2005 he received a contract from the German government to support the development of S/MIME.
Journalists and security professionals rely on GnuPG, and Edward Snowden used it to evade monitoring whilst he leaked classified information from the U.S. National Security Agency.[4] Despite GnuPG’s popularity, Koch has struggled to survive financially, earning about $25,000 US per year since 2001[2] and thus considered abandoning the project and taking a better paying programming job.[4] However, given Snowden’s leaked documents showed the extent of NSA surveillance, Koch continued.[4] In 2014 he held a funding drive and in response received $137,000 US in donations from the public,[2] and Facebook and Stripe each pledged to annually donate $50,000 US to GPG development.[2][5] Unrelated, in 2015 Koch was also awarded a one-time grant of $60,000 US from the Linux Foundation‘s Core Infrastructure Initiative.[5][6]
References
- Wayner, Peter (November 19, 1999). “Germany Awards Grant for Encryption”. The New York Times. Retrieved February 6, 2015.
- Angwin, Julia (February 5, 2015). “The World’s Email Encryption Software Relies on One Guy, Who is Going Broke”. ProPublica. Retrieved February 6, 2015.
- Library Freedom Project and Werner Koch are 2015 Free Software Awards winners FSF
- Goodin, Dan (6 February 2015). “Once-starving GnuPG crypto project gets a windfall. Now comes the hard part”. Ars Technica. Condé Nast. Retrieved 28 July 2015.
- Thomson, Iain (5 February 2015). “Internet lobs $$$s at dev of crucial GPG tool after he runs short of cash”. The Register. Retrieved 6 February 2015.
- Zemlin, Jim (8 February 2015). “Answering the Call for Werner Koch’s Everywhere”. Linux Foundation. Retrieved 28 July 2015.
External links
PRIVACY FOR THE WEAK – TRANSPARENCY FOR THE POWERFUL!
Consider donating to the project: https://gnupg.org/donate/
Aufklärungsfilm: Datenschutz – fast wie Sex
what alternatives are there?
you could use tor-bundle to use a anonymous webmail only service:
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!