NO PANIC!
as the user might know a kernel-panic is just as bad as a human-panic, yes supply chain attacks are bad… very bad… as can be seen with the SolarWinds(hacked)->product for Network management used by many Top100 companies including Micro$oft.
So in theory M$ was hacked by using a software of a vendor that uses auto-update functionality of it’s software.
If the attackers really wanted to distribute havoc around the M$ world… they would have immediately shipped an automatic update to all Windows systems… (which would have installed it automatically… because in Win 10 there is no possibility to turn off automatic updates… anymore (was still possible in Win 7)
So: security of update servers is VERY VERY VERY CRITICAL
“The scenario that Intel system architects, engineers, and security specialists perhaps feared most is now a reality.
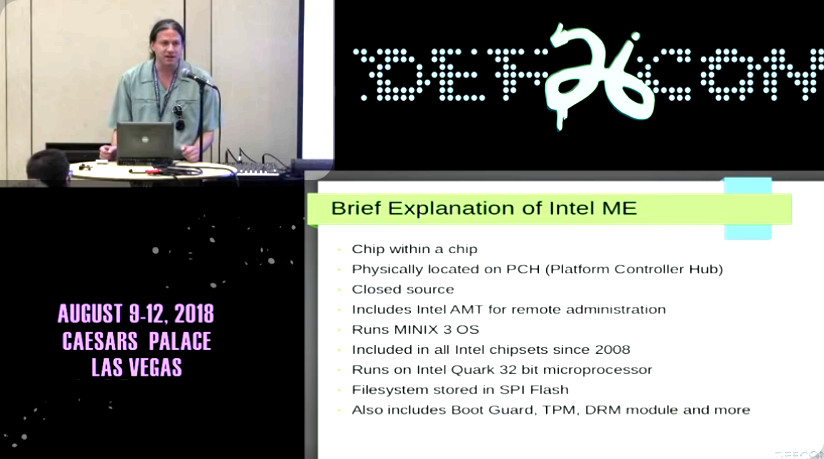
A vulnerability has been found in the ROM of the Intel Converged Security and Management Engine (CSME).
This vulnerability jeopardizes everything Intel has done to build the root of trust and lay a solid security foundation on the company’s platforms.
The problem is not only that it is impossible to fix firmware errors that are hard-coded in the Mask ROM of microprocessors and chipsets.
The larger worry is that, because this vulnerability allows a compromise at the hardware level, it destroys the chain of trust for the platform as a whole.” (src)
The vendors that are careless with security will also suffer severely economically, because customers losing trust in the safety of their products.
So there might be no SolarWinds and even no Intel (!) tomorrow (which yes would be a bit sad, but given the scale of the screwup from spectre to meltdown (by accident, flawed CPU design) to Intel ME (on purpose… but not considering the consequences))
Can Intel restart the trust? Did AMD nothing of such sort? Will ARM CPUs stay hardware-backdoor-free?
“Intel Xeon E3 processors as of today do not have an Intel Manageability” (the plus when buying old servers)
some positive first
the ability to power-cycle a server remotely is nice, and SuperMicro servers for example have such functionality too… (way less hidden from the customer and thus actually of some use)
… allowing even full screen access through the browser via some JavaApplet.
while SuperMicro has the same problem as Intel and other BIOS-vendors: “how to keep this up to date and secure”?
Videos: “GOD MODE”
Minix OS? DAMN YOU Andrew S. Tanenbaum!
ok to set this straight… Tanenbaum does not seem to be complicit, and Intel was simply using his OS for evil without the author’s consent.
“Tanenbaum has declared not having any feedback from Intel about the usage they have made of Minix.”
“But in an open letter to Intel, he explains he was contacted a few years ago by Intel engineers asking many technical questions about Minix and even requesting code change to being able to selectively remove part of the system in order to reduce its footprint.” (src)
“I knew that Intel had some potential interest in MINIX several years ago when one of your engineering teams contacted me about some secret internal project and asked a large number of technical questions about MINIX” (src)
https://devtube.dev-wiki.de/videos/watch/f979469f-5fd1-4c40-a8c4-706c20c001f7
first of: take it serious, but don’t panic!
panic does not help.
popularresistance.org says: New Intel Chips Contain Back-Door Processor, Hackable Even When Computer is Turned Off
“Because AMT allows access to the PC below the OS level, security for the AMT features is a key concern
On May 15, 2017, Intel announced a critical vulnerability in AMT. According to the update “The vulnerability could enable a network attacker to remotely gain access to business PCs or devices that use these technologies”.[43] Intel announced partial availability of a firmware update to patch the vulnerability for some of the affected devices.”(Wiki)
does my computer have Intel Active Management aka Backdoor please hack my system technology?
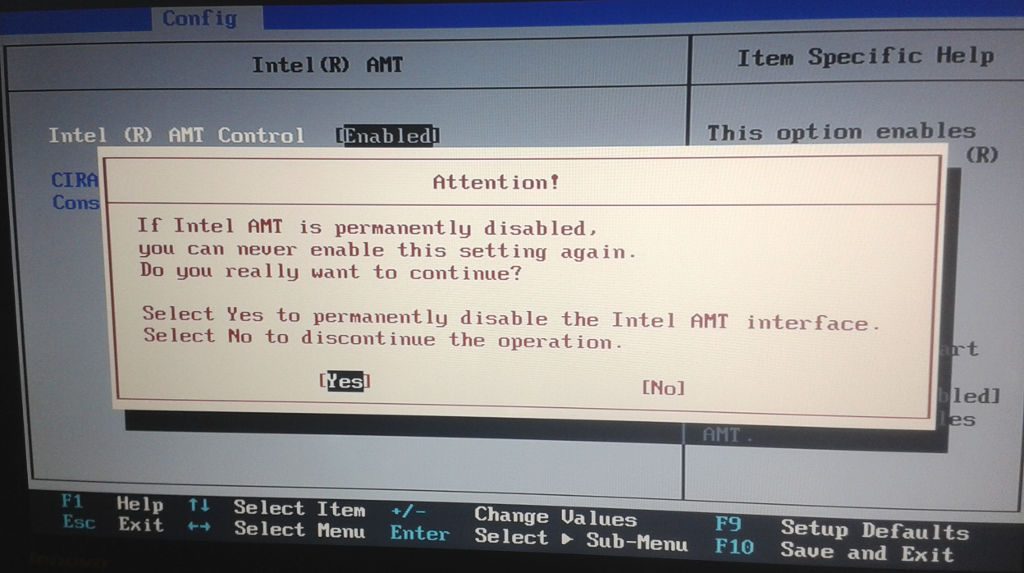
- check your BIOS and any BIOS optionts that allow to disable IntelME, some vendors have included such options
- as gnu linux root the user could try:
su - root; # become root ll /dev|grep mei crw------- 1 root root 244, 0 2021-04-03 mei0 stat /dev/mei0 File: /dev/mei0 Size: 0 Blocks: 0 IO Block: 4096 character special file Device: 6h/6d Inode: 13300 Links: 1 Device type: f4,0 Access: (0600/crw-------) Uid: ( 0/ root) Gid: ( 0/ root) Access: 2021-04-03 17:11:34.279461230 +0200 Modify: 2021-04-03 17:11:34.279461230 +0200 Change: 2021-04-03 17:11:34.279461230 +0200 Birth: - cat /dev/mei0 cat: /dev/mei0: No such device
“An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs:
Intel® Active Management Technology (AMT) and Intel® Standard Manageability (ISM). CVSSv3 9.8 Critical /AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology (SBT). CVSSv3 8.4 High /AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Affected products: The issue has been observed in Intel manageability firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 for Intel® Active Management Technology, Intel® Small Business Technology, and Intel® Standard Manageability. Versions before 6 or after 11.6 are not impacted.”
src: https://github.com/intel/INTEL-SA-00075-Linux-Detection-And-Mitigation-Tools
 “Throw away your computer”
“Throw away your computer”
Julian Assange kept changing hardware for not beeing tracked.
What use is it to install a secure operating system, if your system is already infected with malicious code right after the start of the BIOS?
It is possible for ANY PCI, ISA, PCI-E Device to take full control over all resources during startup.
Therefore it’s also possible for an infected device to load malicious code via internet, every time it starts… leaving no trace on the harddisk, making it impossible for AntiVirus to detect.
Welcome to BAD BIOS 😀 *Muhahahahahahahaha…* (evil laughter of secret agent with hall and fading out)
Jonathan Brossard: “Hardware backdooring is practical” – Security Research Engineer & CEO, Toucan System, France and Australia

Blackhat Briefings and Defcon conferences, Las Vegas, 2012
GET THE PDF 🙂
Links:
WARNING! USE AT OWN RISK ON NON-ESSENTIAL TEST-SYSTEM ONLY! (as it might brick the user’s system): https://github.com/corna/me_cleaner
https://en.wikipedia.org/wiki/Intel_Active_Management_Technology
https://www.reddit.com/r/badBIOS/
Search: https://startpage.com/do/search?q=Rakshasal+backdoor&l=deutsc
Dr Mathias Wagner http://www.nxp.com/countries/germany.html
Chief Security Technologist bei NXP Semiconductors Germany GmbH
http://cybersummit.info/2014/speakers/wagner
http://semiengineering.com/expert-interview-nxp-on-security/
Stealthy Dopant Level Hardware Trojans
http://www.chesworkshop.org/ches2013/presentations/CHES2013_Session4_3.pdf
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!