client
/etc/ssh/ssh_config
is for client side config – here you can for example enable
StrictHostKeyChecking yes
/etc/ssh/ssh_known_hosts
similar to ~/.ssh/known_hosts it contains the system-wide-accepted public keys of other hosts.
So if you have “StrictHostKeyChecking yes” enabled, you could manually accept public ssh keys of other servers via:
ssh-keyscan 172.20.0.12 >> /etc/ssh/ssh_known_hosts
cat known_hosts
172.20.0.12 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBE34/VhKn0tFZQryBgagbahNX2qh2My+ywGfXDNd/rNZRWJcpdr2g0++I6plyMtmahXd2vMU6j03g/Me67xD4C4=
(does not contain the full public key – just a hash of the key of server 0.12)
if the server’s key is not in the list you will get:
“No ECDSA host key is known for 172.20.0.12 and you have requested strict checking.
Host key verification failed.”
server
vi /etc/ssh/sshd_config
is for server side config – here you can specify what auth-meachanism (password or pgp) to use or what users and from what IP’s are allowed to login.
You should disable password auth completely and ONLY user public-private-key authentication.
if you have problems loggin in check the logs…
find /var/log/ -type f \( -name "*" \) ! -path '*.gz*' -exec tail -n0 -f "$file" {} +
sshd[11808]: Authentication refused: bad ownership or modes for directory /home/user/.ssh
solution:
chown -R user:user /home/user/.ssh
chmod 600 /home/user/.ssh/authorized_keys
chmod 700 /home/user/.ssh
tightening security
login to your server, become root… open a second console to test logging in with public keys.
the root-console will stay open even when you restart ssh 🙂
check version running: sshd -v unknown option -- v OpenSSH_7.4p1, OpenSSL 1.0.2k-fips 26 Jan 2017AllowUsers user1 user2 user3 # will allow only those usernames to login vi /etc/ssh/sshd_config; # open up open ssh server config file # only allow user user to login from IP 0.7 0.28 0.12 0.25 user maria may only login from ip 0.7 # if you even want to restrict to certain (fixed) IPs that should be allowed to login go like this: AllowUsers user1@172.20.0.7 user2@172.20.0.28 user3@172.20.0.12 PermitRootLogin no <- should always be no PubkeyAuthentication yes <- use this ONLY to prevent bruteforce attacks ChallengeResponseAuthentication no PasswordAuthentication no <- use this ONLY to prevent bruteforce attacks # WARNING: 'UsePAM no' is not supported in Red Hat Enterprise Linux and may cause several # problems. UsePAM no <- on debian i used to disable this X11Forwarding no <- afaik this should be disabled as well, usually you don't have a gui on your server
:wq; # save and quit in vi
service sshd restart; # restart ssh
test to login from second console
telnet 94.1XX.XXX.XX 22; # will give you the ssh version the server is running... you probably want to hide that
Trying 94.1XX.XXX.XX...
Connected to 94.1XX.XXX.XX.
Escape character is '^]'.
SSH-2.0-OpenSSH_7.4
special tricks:
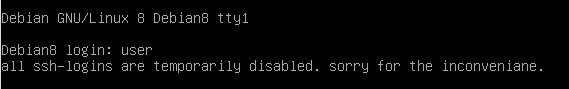
/etc/nologin
echo “all ssh-logins are temporarily disabled until the next reboot. sorry for the inconveniane.” > /etc/nologin
if this file exists – nobody can login – except root directly at a physical server terminal.
the file seems to get automatically deleted on a reboot(debian8.8).
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!