basically the advanced version of PiHole.
WARNING! THIS IS not a complete OPNSense / PFSense tutorial
it is rather just to get started.
right now, one is (still) using iptables without any gui.
there seems to be a lot of documentation on PFSense wich kind of also can be used in OPNSense because OPNSense is a fork of PFSense.
even with OPNSense setting up a custom firewall is not an 3-steps “done in 5min” task.
Just as it-security itself – plan for some iterations:
with iterative i mean, you will have to stay up to day with latest threats again and again.
You will have to repeat answers to theses question again and again:
- Q: is the network secure?
- Q: what possible vectors are there for ransomeware to get in?
- Q: what services are secure / insecure to be used inside the LAN?
- you will have to take some time…
now let’s go: what hardware?
I bought two blade-servers Dell Power Edge R300 and HP ProLiant DL360 on eBay for 100EUR each.
They come with 2-3 NICs, Quadcore-Xeons and plenty of RAM and RAID and dual power supplies.
This might be “overkill” and powerusage is (of course) way beyond (around 100Watts) embedded systems such as the (hopefully soon again available Odroid-H2) will use.
you can also get hardware directly from the producers of OPNSense: https://www.deciso.com/product-catalog/
Whatver hardware you use it needs to have:
- TWO NETWORK CARDS LAN(intranet) and WAN(internet)
- 512MB of RAM (they reommend 4GB)
- be able to run FreeBSD
src: https://docs.opnsense.org/manual/hardware.html
OPNSense is Open Source 🙂 (github src here)
uname -a
FreeBSD OPNsense.localdomain 11.2-RELEASE-p9-HBSD FreeBSD 11.2-RELEASE-p9-HBSD (stable/19.1) amd64
i have very little experience with FreeBSD, while it does not really have bash and the same sets of commands, it is still Unix and seems a pretty good choice for embedded systems (a lot of routers use it).
- very small footprint
- focus on security: “The FreeBSD project includes a security team overseeing all software shipped in the base distribution” … even PlayStation3 and 4 is using it (WTF!?) (src: wikipedia.org)
- great network stack (i was told)
what i really like about OPNSense (at it is probably the same for pfSense)
- it’s Open Source, yes Open Source makes sense, but using PHP on a firewall IMHO does not make sense, because it introduces a lot of security problems. (FritzBox uses lua!? no idea if that is better)
- i really love PHP for it’s easy of use and perfect fit as a server-side web language… but unfortunately it’s purpse is pretty limited to this.
- e.g. searching massive amount of log files is not exactly PHP’s strength, so if you limit PHP usage to display a short set of info that came out of a faster program it might be the right way to use it
- never do anything CPU intensive in PHP, it is not C++ and will stop after 30 sec no matter what.
- even as a transparent-filtering-bridge (TFB) OPNSense gives the Admin a nice look into your LAN’s traffic
- what is going on
- who is communicating with how on what port…
- so you can inspect suspicious traffic, but when it comes to log-inspection it seems we hit a PHP-timeout?
while it is also lacking performance (php 30 sec timeout can not be extended, python does not have a timeout).
it’s not a i386 with 5Mhz,
php is not mentioned here -> https://www.quora.com/Which-is-the-best-programming-language-for-embedded-system
it is actually an “overkill” hardware for a firewall:
sysctl -a | egrep -i 'hw.machine|hw.model|hw.ncpu' hw.machine: amd64 hw.model: Intel(R) Xeon(R) CPU L5410 @ 2.33GHz hw.ncpu: 4 hw.machine_arch: amd64 grep memory /var/run/dmesg.boot real memory = 17179869184 (16384 MB) avail memory = 16575963136 (15808 MB)
Where the name?
The project’s name is derived from open and sense and stands for: “OPeN (source) makes sense”
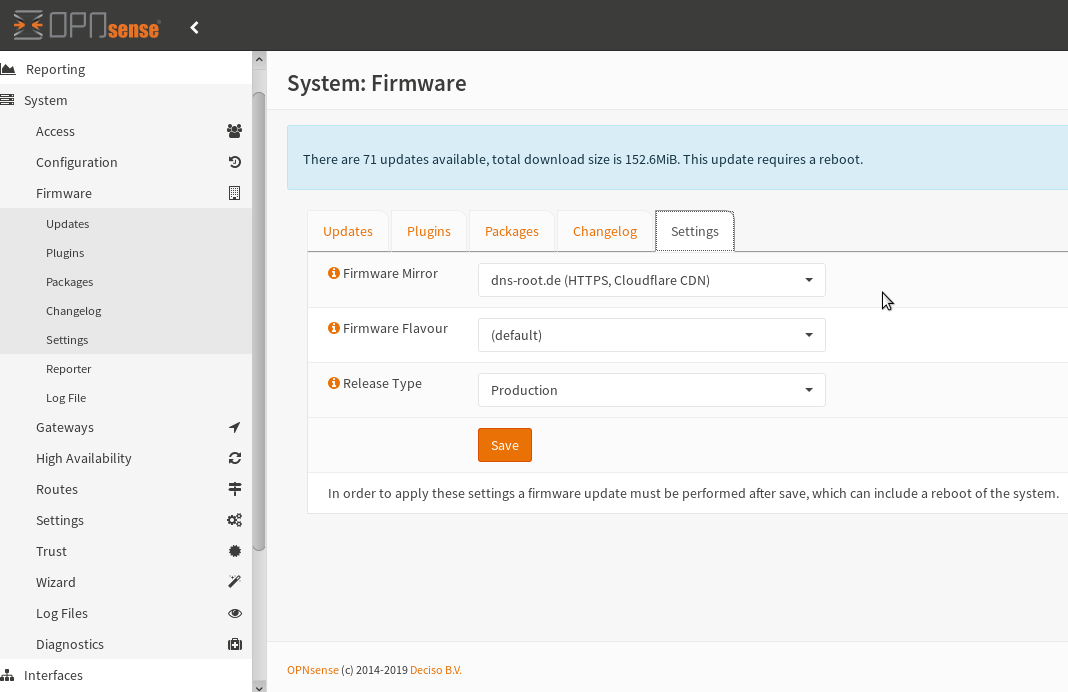
about:
overview/dashboard/lobby/screenshot:
Where to place the firewall in your network?
router/gateway/NAT-firewall mode:
most people will let OPNSense firewall act as DHCP server on LAN and directly hook WAN port towith t a DSL-Modem / Internet-Router / Gateway to “the internet”.
In this case the OPNSense firewall will act as a router between two subnets (192.168.1.X (DSL-Modem) and 192.168.0.X (LAN)
transparent filtering bridge (like a switch) bridging firewall mode:
In my case, this (is right now) not an option, i an existing LanCOM-Router is in use for DHCP and VPN (maybe in the future OPNSense will take the role of DHCP, VPN and Firewall).
So i set it up as “switch” / transparent filtering bridge like this documentation/guide: https://docs.opnsense.org/manual/how-tos/transparent_bridge.html
- “A bridge works by scanning the addresses of MAC level (Ethernet addresses) of the devices connected to each of its network interfaces and then forwarding the traffic between the two networks only if the source and the destination are on different segments. Under many points of view a bridge is similar to an Ethernet switch with only two ports.”
- “A bridge-based firewall can be configured and inserted between the xDSL router and your Ethernet hub/switch without any IP numbering issues.”
- nics must be able to do promiscuous mode (most can)
more to know:
- “Now it is time to create your own file with custom firewall rules, in order to secure the inside network. There will be some complication in doing this because not all of the firewall functionalities are available on bridged packets.
- Furthermore, there is a difference between the packets that are in the process of being forwarded and packets that are being received by the local machine.
- In general, incoming packets are run through the firewall only once, not twice as is normally the case;
- in fact they are filtered only upon receipt, so rules that use “out” or “xmit” will never match.
- Personally, I use “in via” which is an older syntax, but one that has a sense when you read it.
- Another limitation is that you are restricted to use only “pass” or “drop” commands for packets filtered by a bridge.
- Sophisticated things like “divert”, “forward” or “reject” are not available
- Such options can still be used, but only on traffic to or from the bridge machine itself (if it has an IP address).”
- “New in FreeBSD 4.0, is the concept of stateful filtering.
- This is a big improvement for UDP traffic, which typically is a request going out, followed shortly thereafter by a response with the exact same set of IP addresses and port numbers (but with source and destination reversed, of course).
- For firewalls that have no statekeeping, there is almost no way to deal with this sort of traffic as a single session.
- But with a firewall that can “remember” an outgoing UDP packet and, for the next few minutes, allow a response, handling UDP services is trivial.
- The following example shows how to do it. It is possible to do the same thing with TCP packets.
- This allows you to avoid some denial of service attacks and other nasty tricks, but it also typically makes your state table grow quickly in size.”
src: freebsd.org
the bridge will act like a network-switch and connect “WAN” (bge0) and “LAN” (bge1) (which will have NO ip address asigned) to an newly created virtual network device “OPT1” (bridge0) which you can asign an ip that actually can reach “the internet” for updates DNS and so on and so forth.
root@OPNsense:~ # ifconfig em0: flags=8c02<BROADCAST,OACTIVE,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=9b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM> ether 00:15:17:bb:88:6e hwaddr 00:15:17:bb:88:6e nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect status: no carrier em1: flags=8c02<BROADCAST,OACTIVE,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=9b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM> ether 00:15:17:bb:88:6f hwaddr 00:15:17:bb:88:6f nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect status: no carrier bge0: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=c0098<VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,VLAN_HWTSO,LINKSTATE> ether 00:1e:c9:f8:aa:ef hwaddr 00:1e:c9:f8:aa:ef inet6 fe80::21e:c9ff:fef8:aaef%bge0 prefixlen 64 scopeid 0x3 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex,master>) status: active bge1: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=c0098<VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,VLAN_HWTSO,LINKSTATE> ether 00:1e:c9:f8:aa:f0 hwaddr 00:1e:c9:f8:aa:f0 inet6 fe80::21e:c9ff:fef8:aaf0%bge1 prefixlen 64 scopeid 0x4 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT ) status: active enc0: flags=0<> metric 0 mtu 1536 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: enc lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384 options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> inet6 ::1 prefixlen 128 inet6 fe80::1%lo0 prefixlen 64 scopeid 0x6 inet 127.0.0.1 netmask 0xff000000 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> groups: lo pfsync0: flags=0<> metric 0 mtu 1500 groups: pfsync syncpeer: 0.0.0.0 maxupd: 128 defer: off pflog0: flags=100 metric 0 mtu 33160 groups: pflog bridge0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 ether 02:cf:d1:7a:23:00 inet 192.168.0.3 netmask 0xffffff00 broadcast 192.168.0.255 nd6 options=1 groups: bridge id 00:00:00:00:00:00 priority 32768 hellotime 2 fwddelay 15 maxage 20 holdcnt 6 proto rstp maxaddr 2000 timeout 1200 root id 00:00:00:00:00:00 priority 32768 ifcost 0 port 0 member: bge1 flags=143<LEARNING,DISCOVER,AUTOEDGE,AUTOPTP> ifmaxaddr 0 port 4 priority 128 path cost 55 member: bge0 flags=143<LEARNING,DISCOVER,AUTOEDGE,AUTOPTP> ifmaxaddr 0 port 3 priority 128 path cost 55
Warning
The Transparent Filtering Bridge is not compatible with Traffic Shaping.
Do not enable the traffic shaper when using the filtering bridge.
Abstract
A transparent firewall can be used to filter traffic without creating different subnets.
This application is called filtering bridge as it acts as a bridge connection two interfaces and applies filtering rules on top of this.
For more information on Filtering Bridged on FreeBSD, see filtering-bridges
internet not working?
make sure either WAN or “OPT1” bridge have an ip that can reach the dsl-router/gateway.
what about dns?
you could manually config this file and add OpenDNS nameservers 208.67.222.222, 208.67.220.220 or Google DNS Server: 8.8.8.8, 8.8.4.4
root@OPNsense:~ # vi /etc/resolv.conf
domain localdomain
nameserver 127.0.0.1
nameserver 2620:0:ccc::2
nameserver 2620:0:ccd::2
nameserver 208.67.222.222
nameserver 208.67.220.220
You can even use it with OpenDNS (a service that was bought by Cisco in 2015 to filter the web via DNS) in bridge-mode.
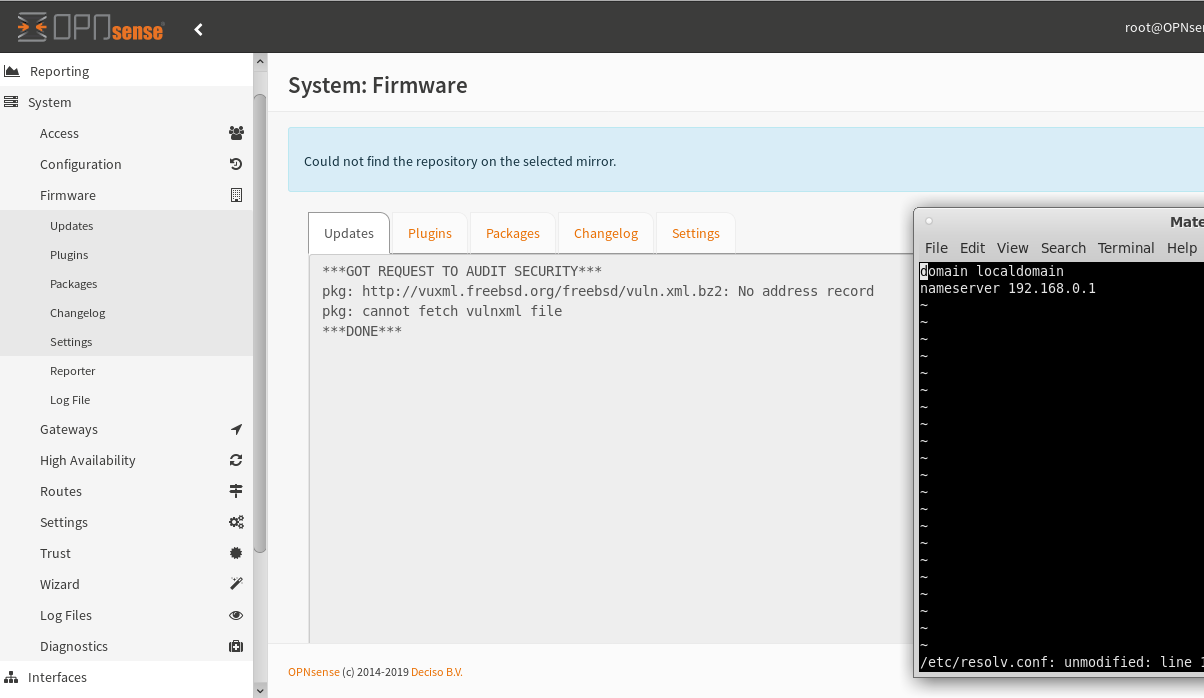
Updates not working?
okay first of all you will have to check if any of your interfaces is ip-wise possible to access the internet/reach your gateway on the WAN port: probably something like 192.168.0.1.
try to select a different mirror
getting started:
- download from: https://opnsense.org/download/
- unzip: bunzip2 OPNsense-18.1.6-OpenSSL-dvd-amd64.iso.bz2
- create a new VirtualBox FreeBSD 64Bit VM and insert the iso
- it will guide you through a live cd run but not install anything on harddisk
https://docs.opnsense.org/manual/install.html
Port Assignments
By default the system will be configured with 2 interfaces LAN & WAN. The first network port found will be configured as LAN and the second will be WAN.
IP ranges & DHCP
The WAN port will have a dhcp client and expects to be assigned an IP adress.
The LAN port will have a dhcp server, a static ip of 192.168.1.1/24 and offers ip adresses in the range of 192.168.1.100-200.
Users & Passwords
Default user: root / password: opnsense
Also good to know
For security reasons ssh is disabled by default and the console access is password protected.
https://wiki.opnsense.org/intro.html
install on harddisk:
- ssh into the box with ssh installer@192.168.0.XX (your box’s ip shown in console)
- it will greet you with this dialog:
- and guide you through setup on disk.
firewall setup:
thanks to Thomas Krenn AG and max-it.de for the cool videos. (sorry right now in German only)
firewall -> aliases
you can block based on ports, ips, ip-lists (URL Table (IPs))
Spamhaus
https://docs.opnsense.org/manual/how-tos/edrop.html
- The Spamhaus Don’t Route Or Peer Lists
-
DROP (Don’t Route Or Peer) and EDROP are advisory “drop all traffic” lists, consisting of netblocks that are “hijacked” or leased by professional spam or cyber-crime operations (used for dissemination of malware, trojan downloaders, botnet controllers). The DROP and EDROP lists are a tiny subset of the SBL, designed for use by firewalls and routing equipment to filter out the malicious traffic from these netblocks.
Source : https://www.spamhaus.org/drop/
- Downloads
https://wiki.opnsense.org/manual/aliases.html
VPN Setup:
misc:
alternative Public DNS Servers:
Public DNS Servers
-
85.214.73.63
-
58.6.115.4258.6.115.43119.31.230.42200.252.98.162217.79.186.14881.89.98.678.159.101.37203.167.220.15382.229.244.191216.87.84.21166.244.95.20207.192.69.15572.14.189.1202001:470:8388:2:20e:2eff:fe63:d4a92001:470:1f07:38b::12001:470:1f10:c6::2001
-
193.58.251.251
recommended reads:
If you don’t know
enough about packet filtering, we suggest that you
take time to read this book:
Building Internet Firewalls, 2nd Edition
Brent Chapman and Elizabeth Zwicky
O’Reilly & Associates, Inc (ISBN 1-56592-871-7)
http://www.ora.com/
http://www.oreilly.com/catalog/fire2/
For a more advanced treatment of Internet Security read:
“Firewalls and Internet Security: Repelling the Wily Hacker, 2nd Edition” by William R. Cheswick, Steven M. Bellowin, Aviel D. Rubin
Addison-Wesley / Prentice Hall (ISBN 0-201-63466-X)
http://www.pearsonhighered.com/
http://www.pearsonhighered.com/educator/academic/product/0,3110,020163466X,00.html
src: vi /etc/rc.firewall
tweets:
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!